The Android NDK supports HWAddress Sanitizer, also known as HWASan, beginning with NDK r21 and Android 10 (API level 29). HWASan is only available on 64-bit Arm devices.
HWASan is a memory error detection tool similar to ASan. Compared to classic ASan, HWASan has:
- Similar CPU overhead (~2x)
- Similar code size overhead (40 – 50%)
- Much smaller RAM overhead (10% – 35%)
HWASan detects the same set of bugs as ASan:
- Stack and heap buffer overflow or underflow
- Heap use after free
- Stack use outside scope
- Double free or wild free
Additionally, HWASan also detects:
- Stack use after return
Sample App
A sample app shows how to configure a build variant for hwasan.
Build
To build your app's native (JNI) code with HWAddress Sanitizer, do the following:
ndk-build
In your Application.mk file:
APP_STL := c++_shared # Or system, or none, but not c++_static.
APP_CFLAGS := -fsanitize=hwaddress -fno-omit-frame-pointer
APP_LDFLAGS := -fsanitize=hwaddress
CMake (Gradle Groovy)
In your module's build.gradle file:
android {
defaultConfig {
externalNativeBuild {
cmake {
# Can also use system or none as ANDROID_STL, but not c++_static.
arguments "-DANDROID_STL=c++_shared"
}
}
}
}
For each target in your CMakeLists.txt:
target_compile_options(${TARGET} PUBLIC -fsanitize=hwaddress -fno-omit-frame-pointer)
target_link_options(${TARGET} PUBLIC -fsanitize=hwaddress)
With NDK 27 or newer, you can also use the following in your build.gradle
and don't have to change CMakeLists.txt:
android {
defaultConfig {
externalNativeBuild {
cmake {
arguments "-DANDROID_SANITIZE=hwaddress"
}
}
}
}
This will not work when using ANDROID_USE_LEGACY_TOOLCHAIN_FILE=false.
CMake (Gradle Kotlin)
In your module's build.gradle file:
android {
defaultConfig {
externalNativeBuild {
cmake {
# Can also use system or none as ANDROID_STL, but not c++_static.
arguments += "-DANDROID_STL=c++_shared"
}
}
}
}
For each target in your CMakeLists.txt:
target_compile_options(${TARGET} PUBLIC -fsanitize=hwaddress -fno-omit-frame-pointer)
target_link_options(${TARGET} PUBLIC -fsanitize=hwaddress)
With NDK 27 or newer, you can also use the following in your build.gradle
and don't have to change CMakeLists.txt:
android {
defaultConfig {
externalNativeBuild {
cmake {
arguments += "-DANDROID_SANITIZE=hwaddress"
}
}
}
}
This will not work when using ANDROID_USE_LEGACY_TOOLCHAIN_FILE=false.
Android 14 or newer: add wrap.sh
If you are running Android 14 or newer, you can use a wrap.sh script to run your debuggable app on any Android-powered device. You can skip this step if you chose to follow the steps in the Setup Instructions.
Follow the instructions to
package a wrap.sh script to add the
following wrap.sh script for arm64-v8a.
#!/system/bin/sh
LD_HWASAN=1 exec "$@"
Run
If you're running on an Android version older than 14, or didn't add a wrap.sh script, follow the Setup Instructions before running your app.
Run the app as usual. When a memory error is detected, an app crashes with
SIGABRT and prints a detailed message to logcat. A copy of the message can
be found in a file under /data/tombstones and looks like this:
ERROR: HWAddressSanitizer: tag-mismatch on address 0x0042a0826510 at pc 0x007b24d90a0c
WRITE of size 1 at 0x0042a0826510 tags: 32/3d (ptr/mem) in thread T0
#0 0x7b24d90a08 (/data/app/com.example.hellohwasan-eRpO2UhYylZaW0P_E0z7vA==/lib/arm64/libnative-lib.so+0x2a08)
#1 0x7b8f1e4ccc (/apex/com.android.art/lib64/libart.so+0x198ccc)
#2 0x7b8f1db364 (/apex/com.android.art/lib64/libart.so+0x18f364)
#3 0x7b8f2ad8d4 (/apex/com.android.art/lib64/libart.so+0x2618d4)
0x0042a0826510 is located 0 bytes to the right of 16-byte region [0x0042a0826500,0x0042a0826510)
allocated here:
#0 0x7b92a322bc (/apex/com.android.runtime/lib64/bionic/libclang_rt.hwasan-aarch64-android.so+0x212bc)
#1 0x7b24d909e0 (/data/app/com.example.hellohwasan-eRpO2UhYylZaW0P_E0z7vA==/lib/arm64/libnative-lib.so+0x29e0)
#2 0x7b8f1e4ccc (/apex/com.android.art/lib64/libart.so+0x198ccc)
The message may be followed by additional debugging information, including the list of live threads in the application, tags of nearby memory allocations and CPU register values.
See Understanding HWASan reports for more information on HWASan error messages.
Building command-line executables
You can build and run executables instrumented with HWASan on Android 14 and newer. You can use the same configuration as described in Build for ndk-build or CMake for your executables. Push the executables to a device running Android 14 or newer and run it as normal using the shell.
If you are using libc++, make sure you are using the shared STL and push it to
the device and set LD_LIBRARY_PATH to the directory containing it when
running your binary.
If you aren't using Gradle, see the NDK documentation to learn how to build from the command line with CMake and ndk-build.
Android 13 or earlier: Setup
If your device runs Android 14 or newer, you can skip this step and follow the instructions for using wrap.sh in the Build section. You can also choose to follow this section and skip the instructions for using wrap.sh.
Before Android 14, HWASan applications need a HWASan build of Android to run. You can flash prebuilt HWASan images to supported Pixel devices. The builds are available on ci.android.com, where you can click the square for the exact build you want to get a Flash Build link. This requires that you know the codename for your phone.
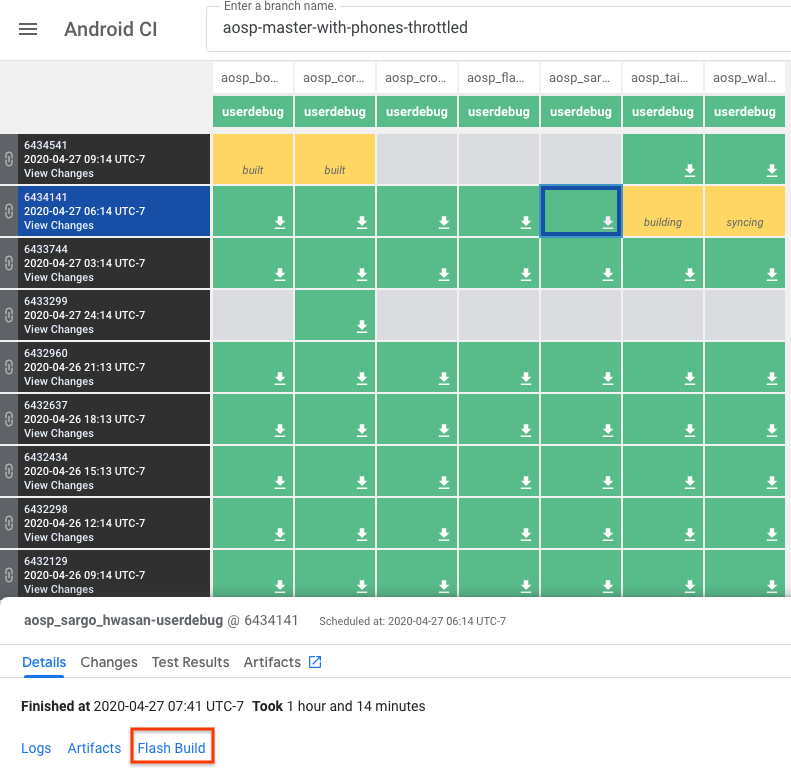
It may be easier to instead go straight to flash.android.com because there the flow starts with detecting your device and only shows you builds you can use. The following images illustrate the setup flow in this tool.
Enable developer mode on your device and connect it to your computer using a USB cable. Click Add new device, select your device from the dialog, and click Connect.
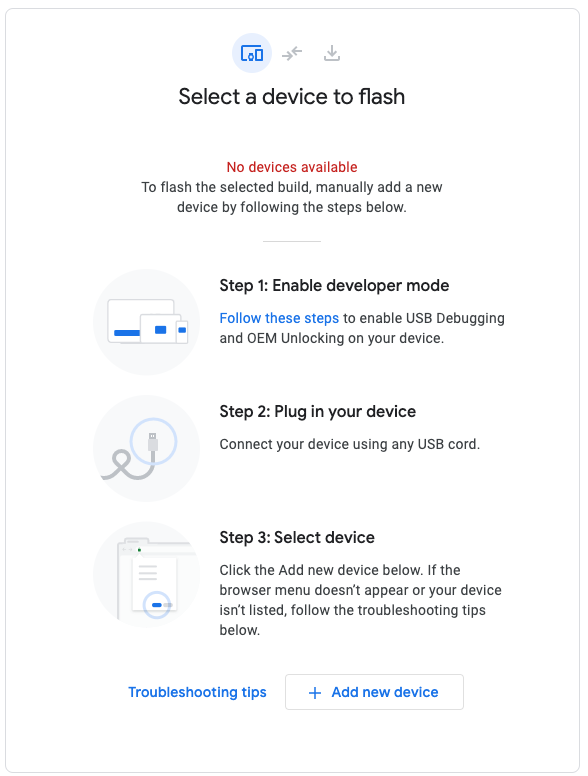
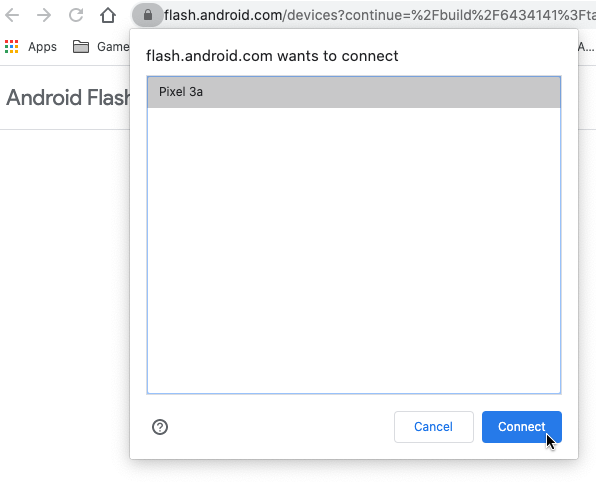
After your device is connected, click it to configure the build.
In the Select a build ID box, select the aosp-master-with-phones-throttled
branch to automatically choose the correct image for the device you have
connected.
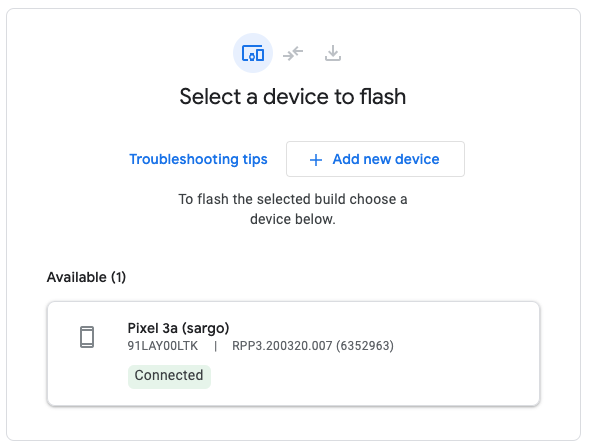
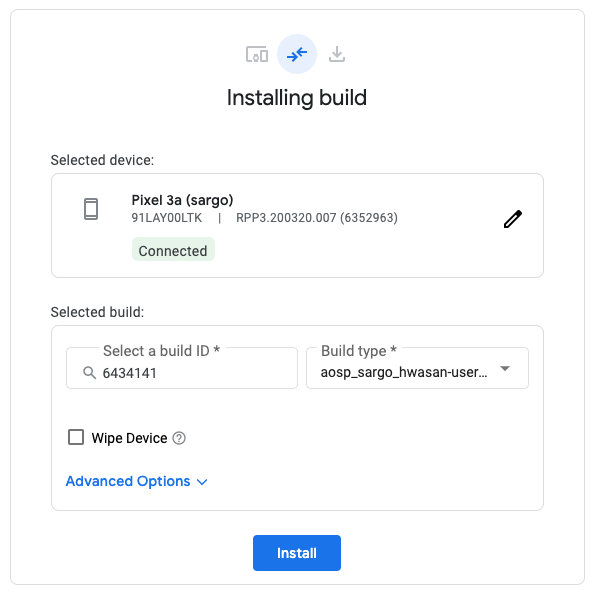
Click Install to flash your device.
There's more detail about the necessary set up in the Android Flash Tool documentation. Alternatively, you can check the AOSP documentation for instructions for building a HWASan image from source.
